Security Resource Center for Mac-Based Businesses
Confused about cybersecurity?
You’re not alone.
This free resource center is designed to help Mac-based businesses improve their security posture, understand compliance risks, and protect their data — without the tech overwhelm.
Macs are secure by design, but they can't protect you from phishing, social engineering, or costly miscommunication. That’s where we come in.
Why Mac-Based Businesses Can’t Ignore Cybersecurity
Contrary to popular belief, Macs are not immune to cyber threats. From ransomware to phishing and insider risks, Mac-based businesses face increasing pressure to protect data, secure devices, and meet compliance demands.
Here’s what’s at stake:
- Customer trust and reputation
- Regulatory fines (FTC, IRS, HIPAA, etc.)
- Downtime that halts business operations
- Financial losses from scams and breaches
And no — being on a Mac doesn’t protect you from being tricked, targeted, or compromised. Most cyberattacks today aren’t about the device — they target the tools you use every day like email, messaging apps, and cloud services. It’s no longer just about viruses — it’s about people being misled into giving access away.
FREE TOOLS & DOWNLOADS
Here are free, practical tools you can download today to improve your business’s security posture:
Security & Compliance Checklist (Email Required)
A one-page checklist to assess whether your Mac-based business meets core security expectations.
Mac Security Roadmap (Direct Download)
A visual guide to help your team focus on the first 5–7 essential actions.
Incident Response Quick Guide (Direct Download)
What to do in the first 24 hours if you suspect a breach.
Cybersecurity Budget Estimator (Direct Download)
A simple worksheet to help you plan next year’s IT/security investment.
Case Study: Unprotected File Sharing Led to Major Exposure (Direct Download)
A small medical non-profit came to us after their data was exposed through a shared folder link that was accessed via email. There were no security policies in place — it was the wild west internally, with every employee using tools and sharing sensitive files however they liked.
TRUSTED SECURITY FRAMEWORKS
Explore these nationally recognized cybersecurity resources to support your internal policies, awareness training, and strategic planning:
Government-Endorsed Cybersecurity Resources
- NIST Cybersecurity Framework — The foundational standard for risk-based cybersecurity planning.
- CIS Controls v8 — A prioritized set of actions to protect against the most common cyber threats.
- CISA Free Cybersecurity Tools — Tools and guidance from the U.S. Department of Homeland Security for small and medium businesses.
- FTC Cybersecurity for Small Business — Practical cybersecurity tips covering phishing, password protection, and ransomware.
- SBA Cyber Safety for Small Business Owners — Best practices from the U.S. Small Business Administration for business owners.
- NIST Small Business Cybersecurity Corner — Clear guides and resources tailored to small business security planning.
These trusted frameworks and agencies provide free tools, checklists, and training materials you can use right now to build a safer business environment — no IT team required.(https://www.nist.gov/cyberframework)
APPLE-ALIGNED MAC SECURITY
We follow and expand on Apple’s own security best practices. Apple builds world-class security into every Mac — our job is to take that even further with managed protection, monitoring, compliance support, and proactive helpdesk coverage to keep your systems locked down and running smoothly.
Below are two core Apple resources that align with our security philosophy:
- Set up your Mac to be secure
Apple’s official checklist for hardening your Mac — passwords, admin controls, system settings, and more.
- Protect your Mac from malware
Apple’s guide to avoiding malicious software and ensuring apps are safe and trusted.
MAC-FOCUSED SECURITY FAQs
Top questions we hear from Mac-first business owners:
Q1. Are Macs really safer than PCs?
Yes — and there’s data to support it. IBM reported that PC users generated twice as many support tickets as Mac users, and that Macs experienced fewer security incidents overall. (source)
However, being on a Mac doesn’t make you immune to phishing, social engineering, or insider mistakes. These threats target behavior — not your operating system — which is why every business needs a full security program, regardless of device. (source)
Q2. What cybersecurity tools should Mac-based teams use?
EDR software, DNS filtering, secure backups, and MDM (mobile device management) — all macOS-compatible.
Q3. Do Macs need antivirus?
Yes — ideally lightweight, Apple-friendly antivirus that doesn’t interfere with performance.
Q4. What compliance laws apply to my business?
It depends on your industry — common frameworks include HIPAA, IRS Pub 4557, FTC Safeguards, and PCI.
Q5. Can you help us get compliant?
Absolutely. We guide Mac-based teams through assessment, remediation, and documentation steps for compliance.
Q6. Why do hackers go after small businesses?
Because they know most small businesses aren’t prepared. You're seen as a soft target with valuable data. (source)
Q7. Which threats are we most likely to face as a small business?
Phishing emails, business email compromise, ransomware, and social engineering are among the top threats today. (source)
Q8. Do I need a dedicated cybersecurity team or can I outsource?
Outsourcing to a security-focused, Mac-native partner like us is a great way to stay protected without hiring full-time staff. (source)
Q9. What basic security controls should every Mac-based business have?
Start with endpoint protection, secure backups, staff training, MFA, DNS filtering, and documented policies. (source)
Q10. How much should we spend on cybersecurity?
It depends on your size, industry, and exposure — but even small teams need to budget for prevention, not just reaction. Our free budget estimator tool can help you model it realistically.
Q11. Do Macs Get Viruses?
Hang on—this is a big topic, and I’ll keep it as short as possible. But if you’re here, it’s because you want the truth. Stick with me and you’ll be glad you did.
macOS is a UNIX-based operating system, and like other UNIX platforms, it
benefits from built-in protections against many traditional computer
viruses. In addition to those UNIX strengths, Apple has built powerful
safeguards like Gatekeeper, System Integrity Protection (SIP), and built-in
malware detection into every Mac.
That said, while true computer viruses (the old-school kind that spread
automatically) are rare on modern Macs, your Mac is absolutely still at
risk from other digital threats—especially the kind targeted at users, not
systems.
Q12. Do Macs Need Antivirus or Security Software?
Yes—because malware, adware, spyware, ransomware, phishing attacks, and browser hijackers do target Macs. These may not be "viruses" in the traditional sense, but they can still do serious damage or compromise your business.
The good news is, modern endpoint security tools (what most people call antivirus) do much more than scan for viruses. They protect against all kinds of digital threats—including the ones most likely to affect Mac users. These tools also help prevent your Mac from accidentally spreading infected files to others on your network, especially if your clients or coworkers use Windows PCs.
Bottom line: You don’t need just any antivirus tool—you need *advanced endpoint protection* that works proactively to prevent attacks, not just react after something’s gone wrong. If your work involves client data, remote access, or compliance standards (HIPAA, SOC2, etc.), solid Mac security isn’t optional—it’s your responsibility.

Why Being on a Mac Doesn’t Mean You’re Safe
Helping Mac-based businesses in Minneapolis and across the U.S. stay secure — here's what happens when teams underestimate people-based threats:
Being a Mac-based business is smart — fewer viruses, fewer compatibility issues, and greater security by design. But nearly every case we respond to isn’t about malware. It’s about phishing, social engineering, and human error — all platform-agnostic.
- A Minneapolis-based creative agency running 100% on Macs lost $64,000 when employee credentials were leaked. The attacker followed up with a social engineering phone call impersonating a bank, and gained access to funds.
- Another Minneapolis company — fully Mac-based — had a hacker silently monitor emails for weeks. When a vendor payment was due, the attacker altered the routing details and rerouted $40,000 into their own account — undetected until it was too late.
- We get weekly calls from Mac users — business owners, retirees, and remote workers — who’ve lost $2,000–$2,500 to fake virus alerts, phishing emails, and scam tech support calls.
- We’ve seen many residential and solopreneur clients using Macs pay thousands per year in duplicate services — overlapping antivirus, cloud backup, or streaming subscriptions they didn’t understand or need. They weren’t hacked, but they were unsupported — and that cost them too.
Bottom line: Macs reduce risk, but they don’t eliminate it. Cybersecurity isn’t about your device — it’s about what you click, trust, and assume is safe.
Free Security Webinar for Your Team
Mac-based businesses face unique risks — and most don’t even realize what’s missing until it’s too late.
In this 30-minute session, we’ll walk your team through the 5 most critical security controls every small business should have in place — no jargon, no scare tactics, just practical advice.
Qualifying businesses can book a free webinar here
Perfect for internal awareness, team onboarding, or leadership education.
USEFUL SECURITY TOOLS
Test Your Password Strength
Hackers today use AI-powered brute force tools and stolen credential databases to crack weak passwords in seconds. That’s why every password should be:
- At least 12 characters long (longer is better)
- Include upper and lowercase letters
- Include numbers and special characters
➡️ Try it: Password Strength Checker
We understand that remembering dozens of strong passwords is impossible without a password manager — that’s why we help our clients implement secure, easy-to-use password management systems.
Not sure where to start with a password manager or team training?
👉 Book a discovery call — we can help you put the right system in place.
— that’s why we help our clients implement secure, easy-to-use password management systems.
Check Your Email Security Settings (DKIM, SPF, DMARC)
Email spoofing and phishing attacks often succeed when your email system isn’t configured with proper domain protections. These records help email providers verify your messages are really from you.
Not sure if yours are working?
➡️ Test here: DKIM/DMARC/SPF Checker
If your records aren't set up properly, you may be more vulnerable to impersonation and email delivery issues.
Need help setting this up correctly?
👉 Book a discovery call — we’ll walk you through it.
REAL SCAMS FROM REAL MAC USERS
We’ve collected real-world screenshots of scams that have targeted Mac users — including phishing emails, fake pop-ups, and social engineering attempts. These are the types of threats our clients face every day.
Each example includes a short caption explaining what’s wrong and how to spot it.
Click on the image to enlarge
Fake Blue Screen Pop-Up – “Critical System Failure” Scam
Description: This fake blue screen alert mimics a system crash (on a PC) and claims your computer is critically damaged. It urges you to call a “technician” to prevent data loss — but the number connects you to scammers, not real support.
️Warning: This is a scare tactic. If you see a pop-up like this, force-quit your browser. Never call the number or allow remote access.
Risk if you fall for it: You may be tricked into installing malware, handing over sensitive info, or paying for bogus “repairs.” Scammers may even lock you out of your Mac or steal personal and financial data.
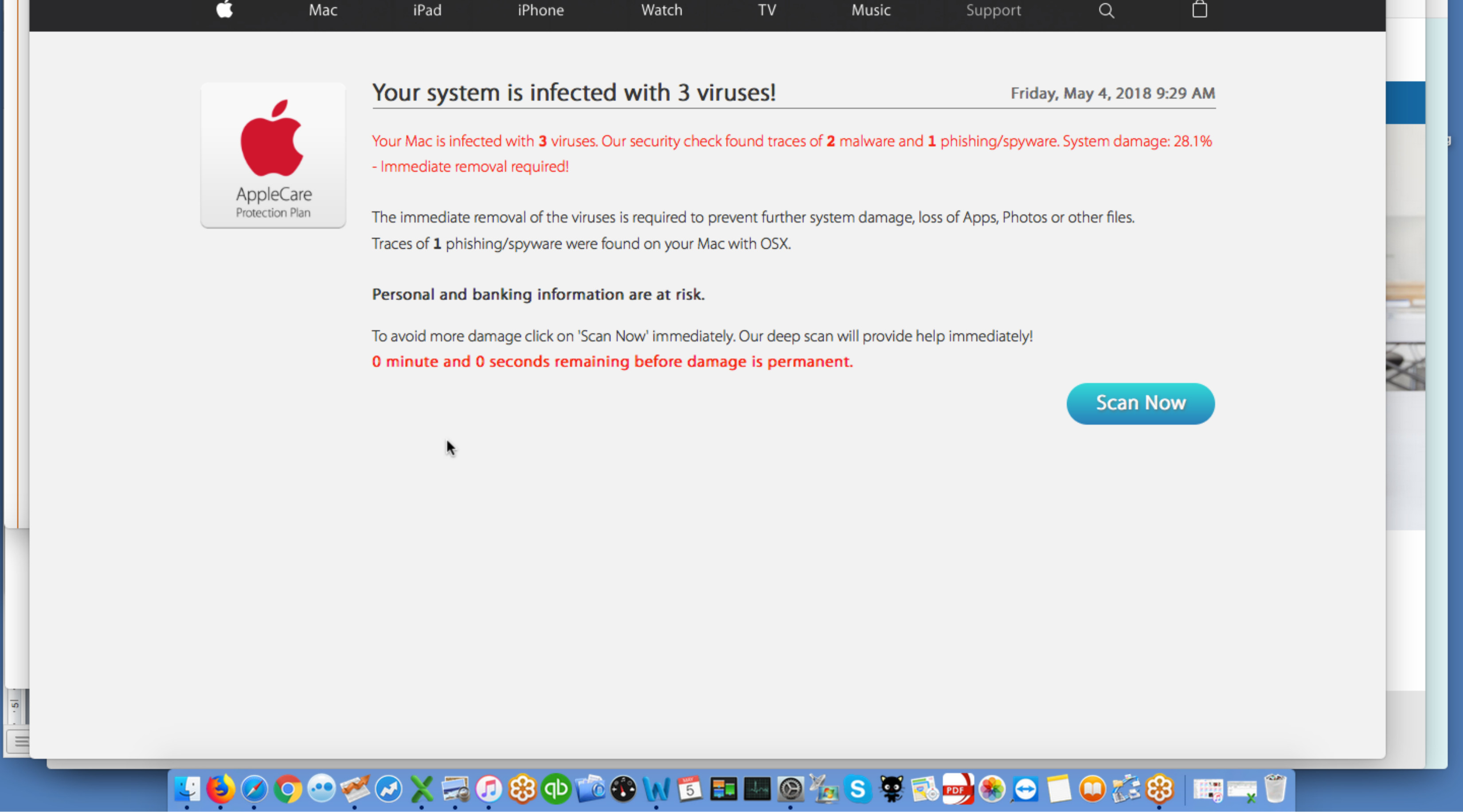
Fake Apple Virus Alert – “Scan Now” Pop-Up
Description: A fake AppleCare warning says your Mac is infected with “3 viruses” and urges you to click “Scan Now.” It mimics Apple’s design but is completely fake and meant to scare you into downloading harmful software or giving up personal info.
️Warning: Apple will never use pop-ups to alert you of viruses or ask you to run a scan. Close your browser immediately and do not click anything.
Risk if you fall for it: Clicking may lead to malware installation, scamware that demands payment, or phishing attempts to collect your banking and personal info.
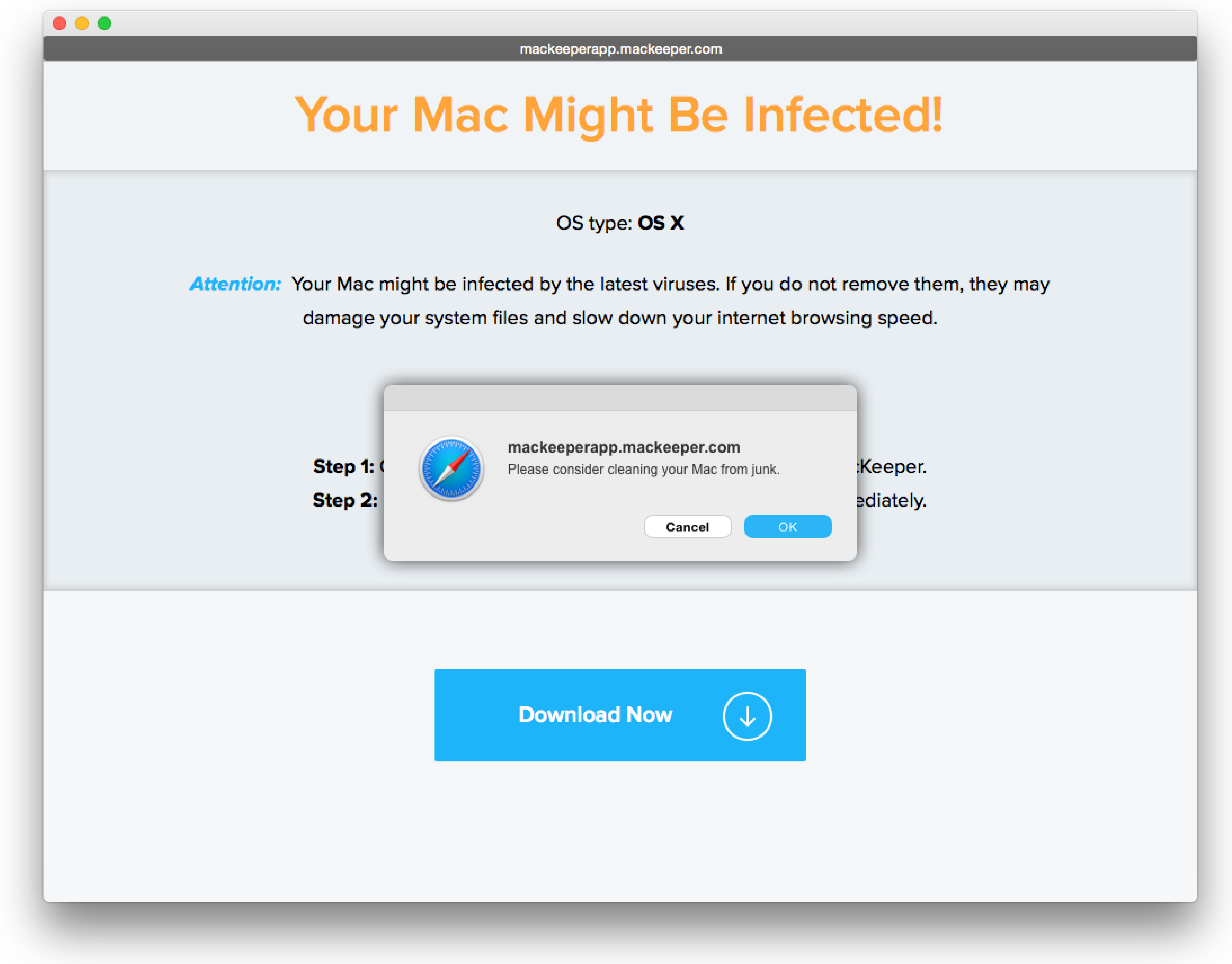
Fake Mac Virus Alert Pop-Up
Description: A fake website or pop-up warns that your Mac is “infected” and urges you to download cleanup software. It’s designed to scare you into installing junkware — or worse.
️ Warning: Do not click "Download" or install anything from pop-ups. Always use trusted sources like the Mac App Store or official vendor sites.
Risk if you fall for it: You could install scamware that slows down your Mac, harvests your data, or opens the door to malware. In some cases, these fake tools demand payment to “fix” problems that don’t exist.
Fake PayPal Invoice – Bitcoin Renewal Scam
Description: A fake invoice email claims you’ve been charged $417 for a Bitcoin subscription through PayPal and urges you to call a “support” number to cancel. It’s designed to scare you into calling a scammer who will try to access your device or financial info.
️ Warning: Never call the number on a suspicious invoice. Log into your real PayPal account directly to confirm charges — if it’s not listed there, it’s fake.
Risk if you fall for it: You may unknowingly give scammers remote access, banking details, or personal data. Some victims have lost hundreds or thousands through social engineering and fake refunds.
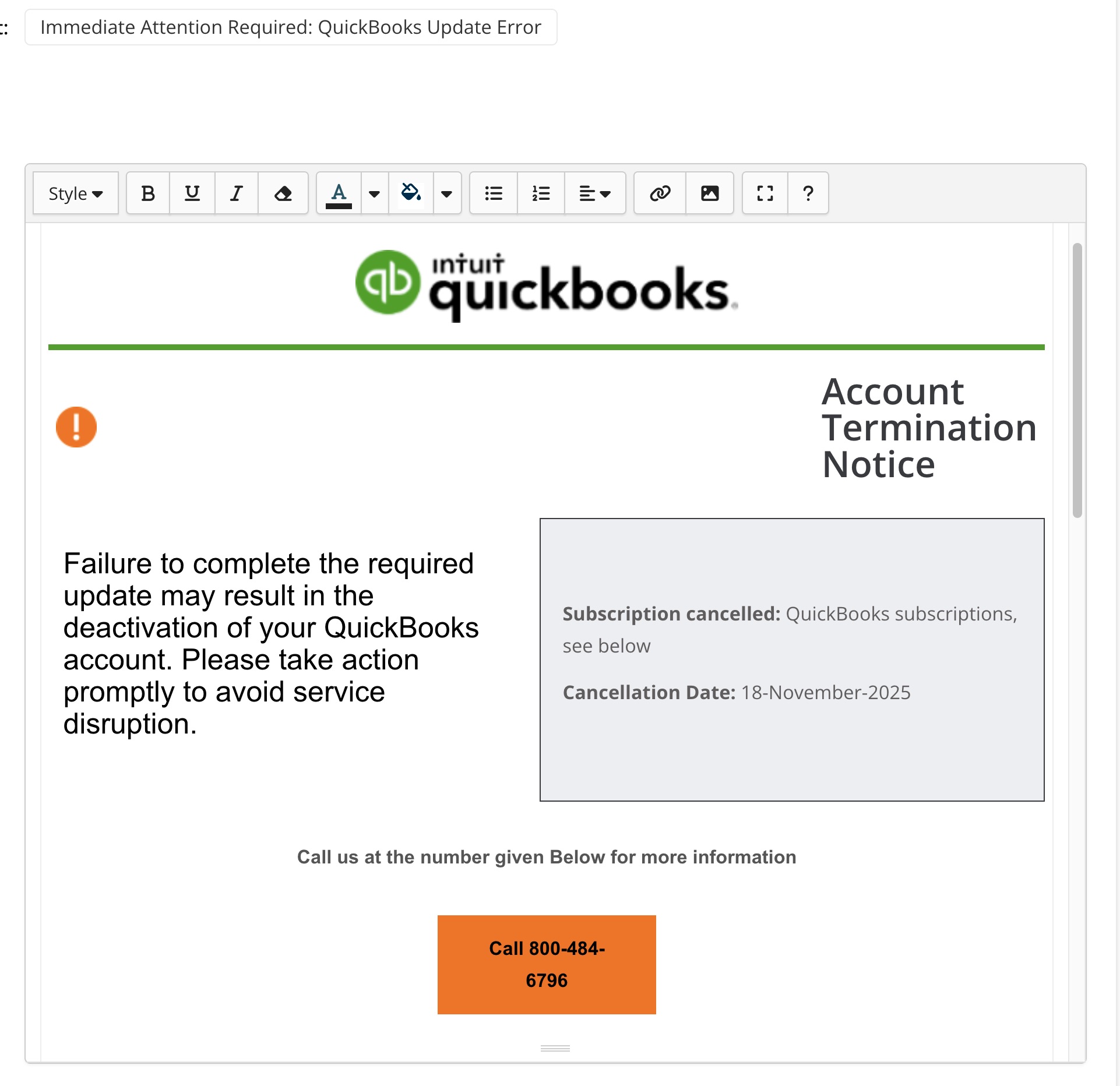
QuickBooks Account Termination Scam
Description: Fake email claims your QuickBooks subscription is cancelled and urges you to call a support number. Scammers try to steal your login or gain remote access to your Mac.
Warning: Don’t call these numbers. Always log into your QuickBooks account directly — never trust links or phone numbers in email alerts.
Risk if you fall for it: You could expose your entire accounting system, giving attackers access to bank accounts, payroll data, tax records, and client billing info. Losses can happen instantly — and often aren’t recoverable.
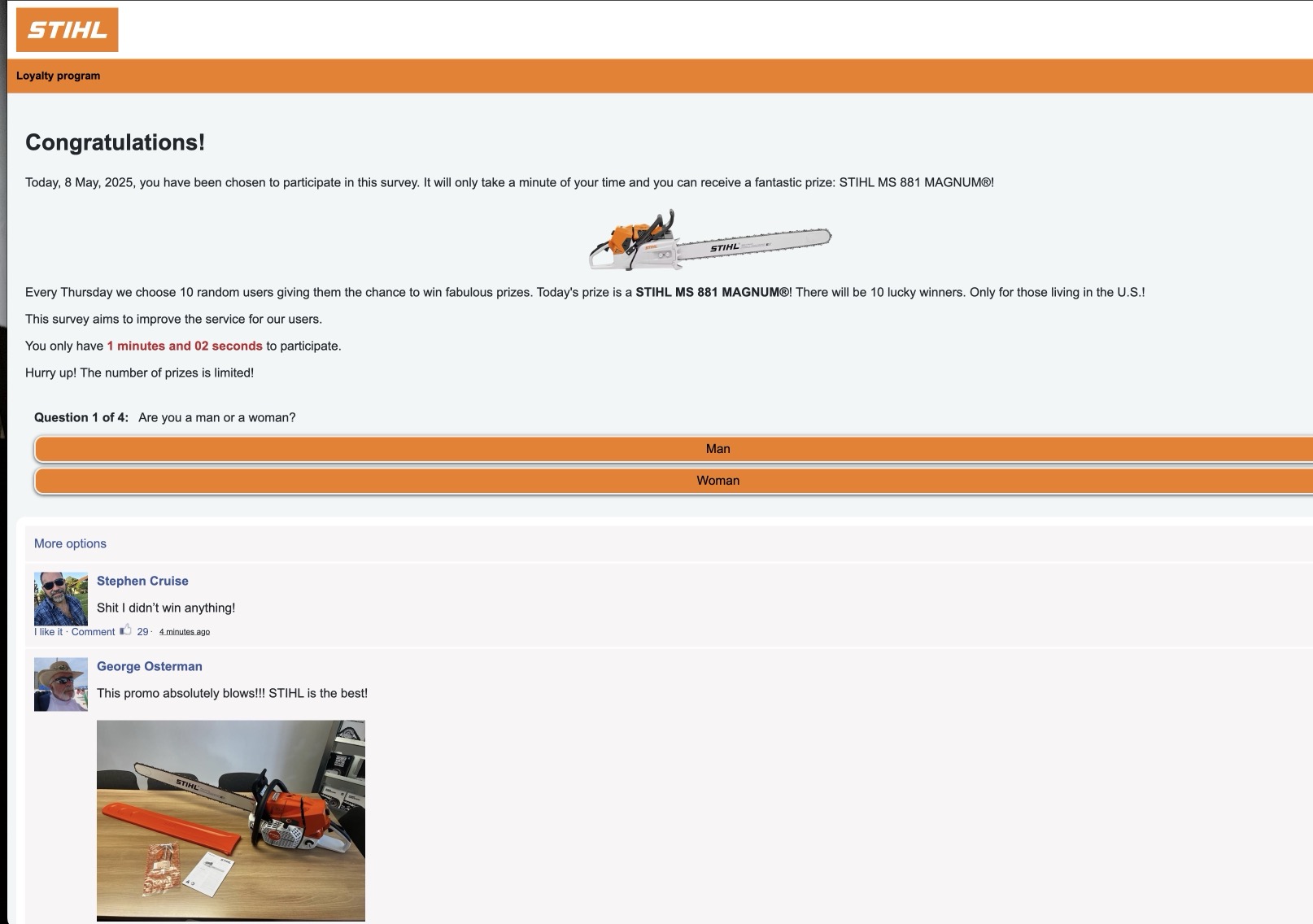
Too Good to Be True – Fake STIHL Chainsaw Giveaway
Description: This scam often appears in Facebook ads or posts, claiming you've been chosen to win a STIHL MS 881 MAGNUM® chainsaw. It uses a fake survey, countdown timer, and phony social media comments to build false urgency and trust.
️Warning: STIHL is not giving away chainsaws in random online surveys. These are scams designed to collect your personal info or credit card data. Never enter information in these popups or links from social media.
Risk if you fall for it: You could give away sensitive personal details, receive fake charges, or have your credit card info sold. These scams often lead to identity theft and ongoing spam/phishing.
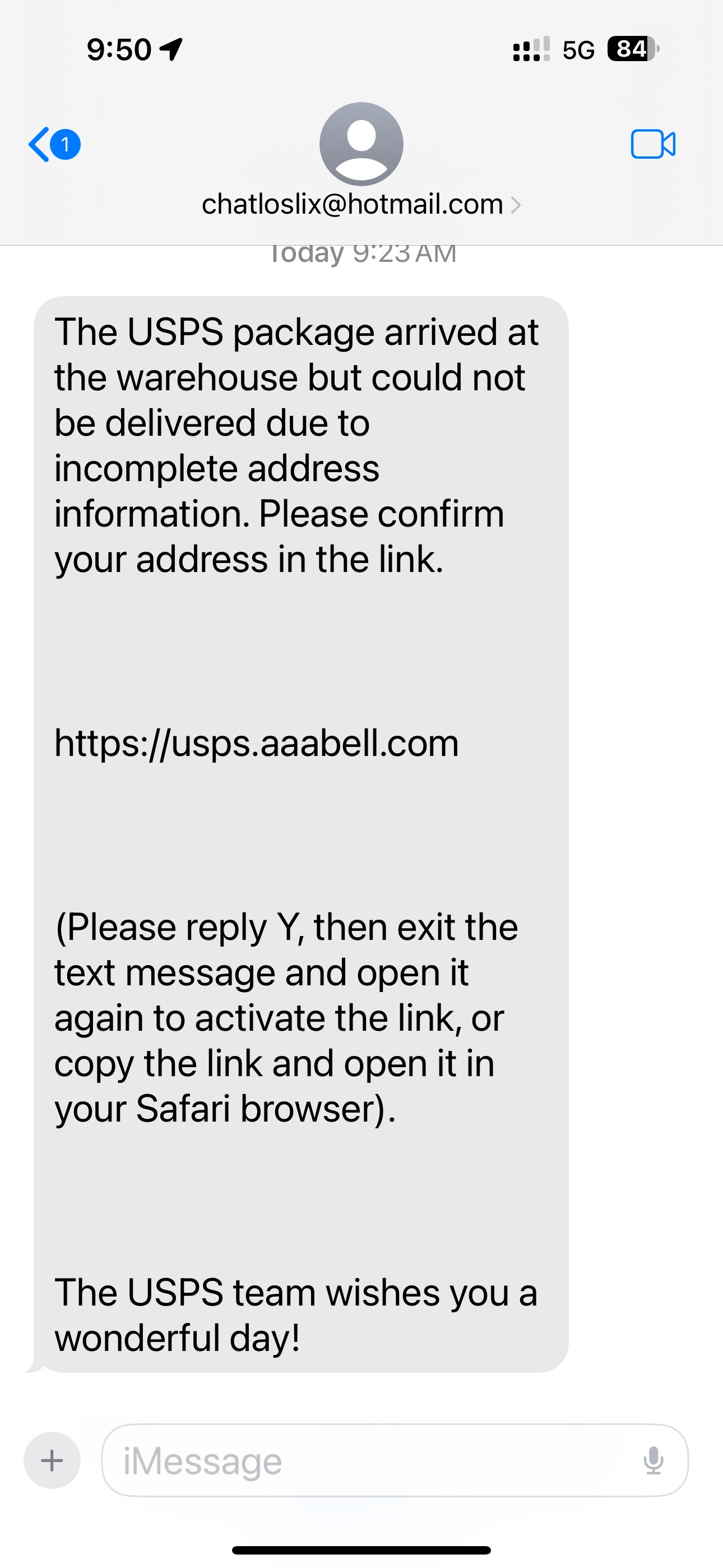
USPS Delivery Failure Text Scam
Description: This fake text message claims a USPS package couldn’t be delivered due to an “incomplete address” and asks you to click a link to update your info. These often appear from sketchy email addresses (like a Hotmail account) instead of a real USPS number.
️Warning: The USPS will never ask you to update delivery info through a link in a random text. Always go to usps.com
Risk if you fall for it: You could end up entering personal info (like your address or credit card) on a spoofed site. This may lead to identity theft, fraud, or unauthorized charges.
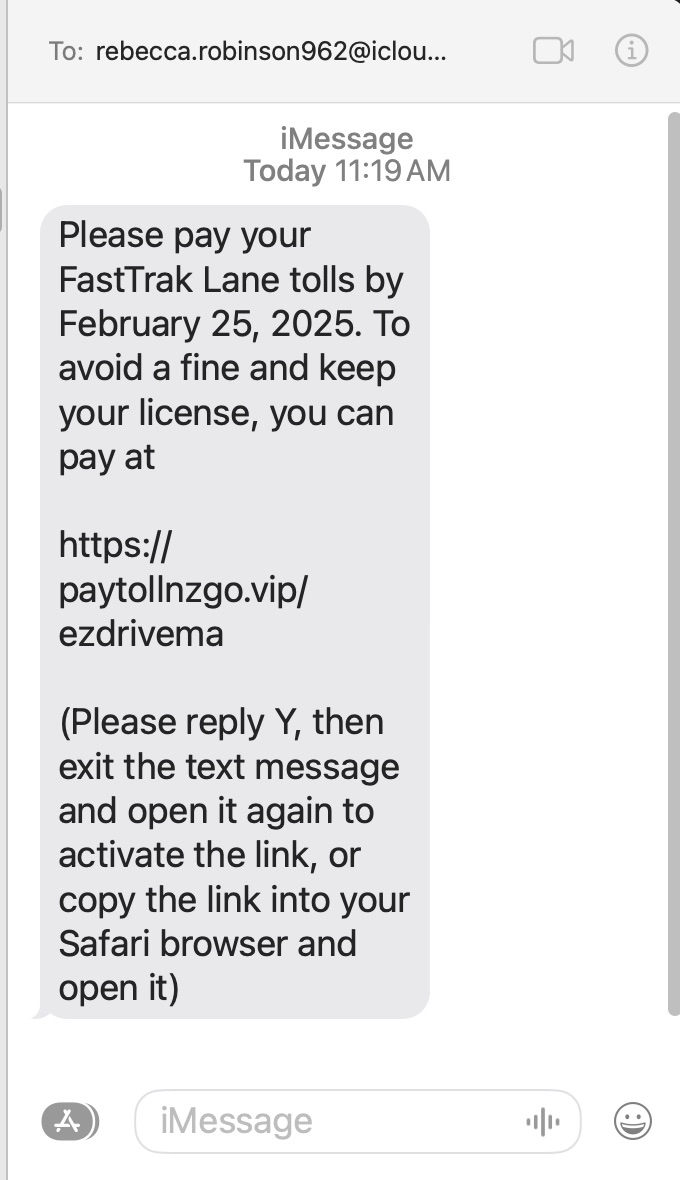
Toll Payment Text Scam
Description: A fake message pretending to be from a toll agency like EZPass or FastTrak. It threatens fines or license suspension unless you pay immediately using a sketchy link like paytollnzgo.vip. These scams are widespread and designed to cause panic.
️Warning: No legitimate toll agency will threaten you by text or demand urgent payment via strange URLs. Always log in to your official toll provider’s site or app to verify any notices.
Risk if you fall for it: Scammers can collect your credit card details, personal info, or even access online banking if reused passwords are involved — leading to direct financial loss and identity theft.
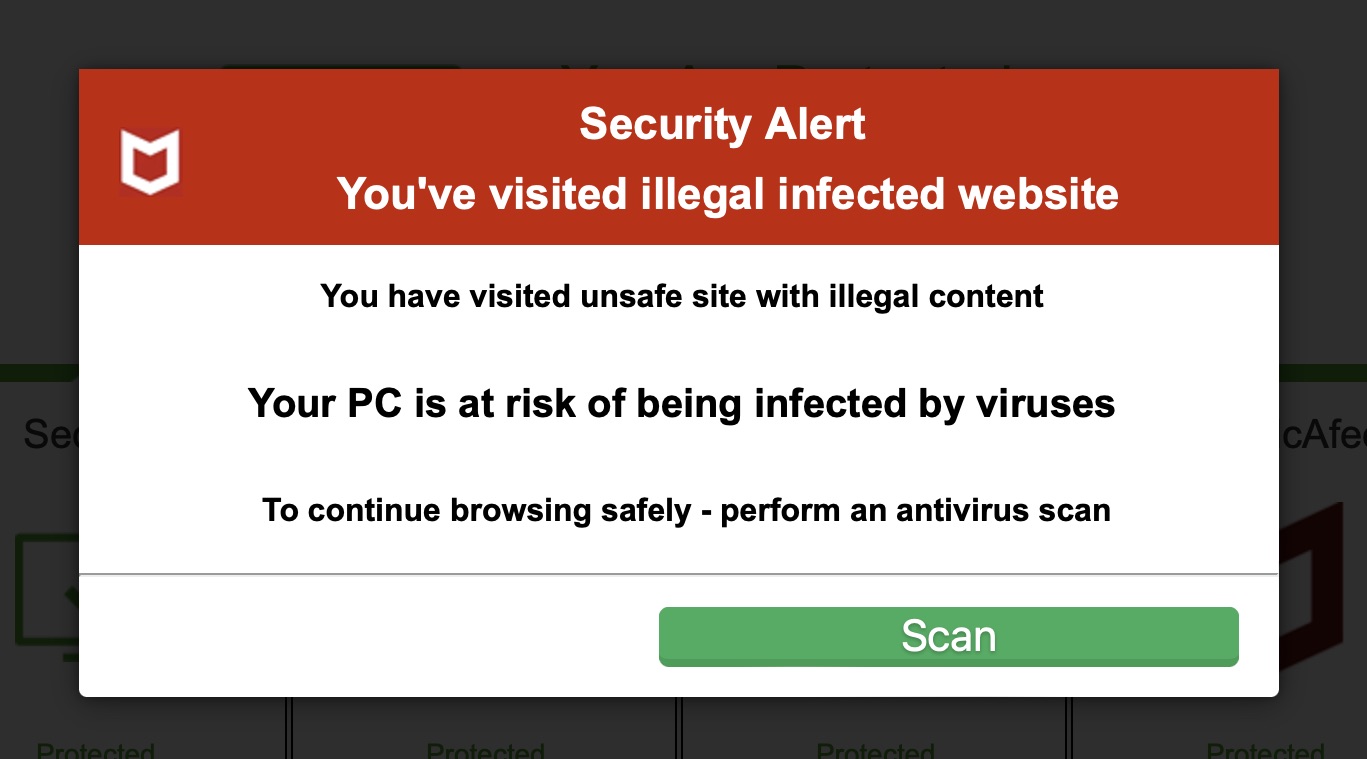
Fake Antivirus Pop-Up — “Illegal Infected Website” Warning
Description: This pop-up mimics a legitimate antivirus warning (pretending to be from McAfee or another brand) and claims you’ve visited an illegal or infected website. It tries to scare users into clicking “Scan,” which usually installs malware or redirects to a scam site.
️Warning: These are fake pop-ups, not legitimate system alerts. Real antivirus software will never alert you through a browser window or demand immediate scans. If in doubt, close the browser tab and run your trusted antivirus manually.
Risk if you fall for it: Clicking could install spyware, steal passwords, lock you out of your system, or trick you into purchasing fake "cleanup tools" — leading to financial loss and identity theft.
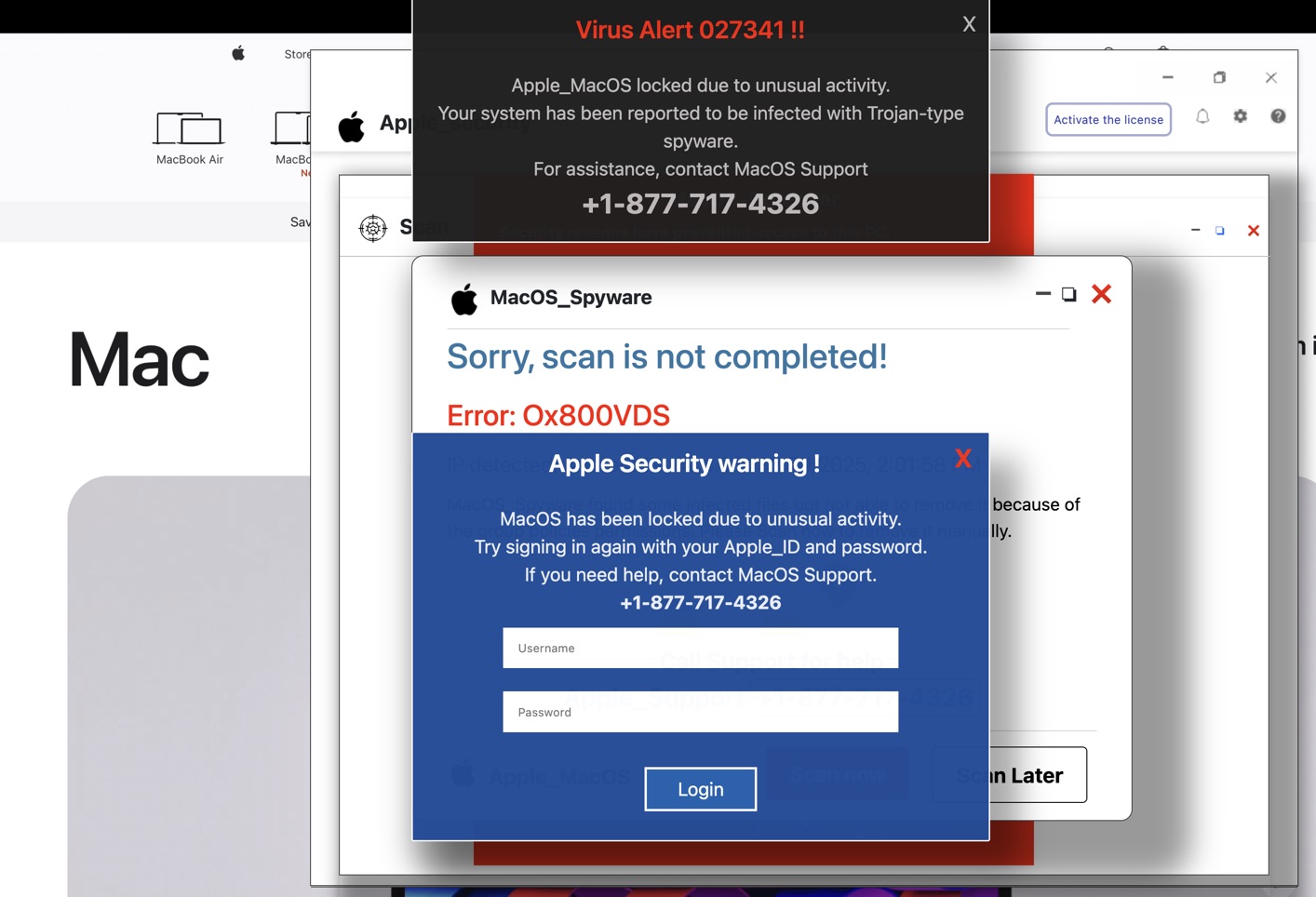
Apple ID Phishing Pop-Up — “MacOS Locked Due to Unusual Activity”
Description: This multi-layered pop-up simulates system alerts claiming your Mac is locked and infected with spyware. It urges users to enter their Apple ID and password or call a fake Mac support number. None of this is real.
️Warning: These messages are not from Apple. Apple will never lock your device this way or ask for your credentials through a pop-up. Never enter your Apple ID or password in pop-ups like this — close the browser immediately and run a security scan if you’re unsure.
Risk if you fall for it: If scammers get your Apple ID, they can access your entire digital life: contacts, photos, files, emails, saved passwords, and App Store purchases. It's a major compromise.
TIP: Enable 2FA (two-factor authentication) on your Apple ID to prevent unauthorized access.
Have a suspicious message or pop-up?
Send it to us — we’ll help you identify it.
Ready to Secure Your Mac-Based Business?
If you have questions about anything on this page or need help deciding what steps to take next, feel free to reach out — we're here to help.
And don’t forget: you can download any of the tools and checklists above to start improving your security today.